Harvard University’s vision for enterprise architecture is to articulate and drive to common solutions, standards, and opportunities for alignment in order to reduce IT complexity and cost across the University and enable local innovation.
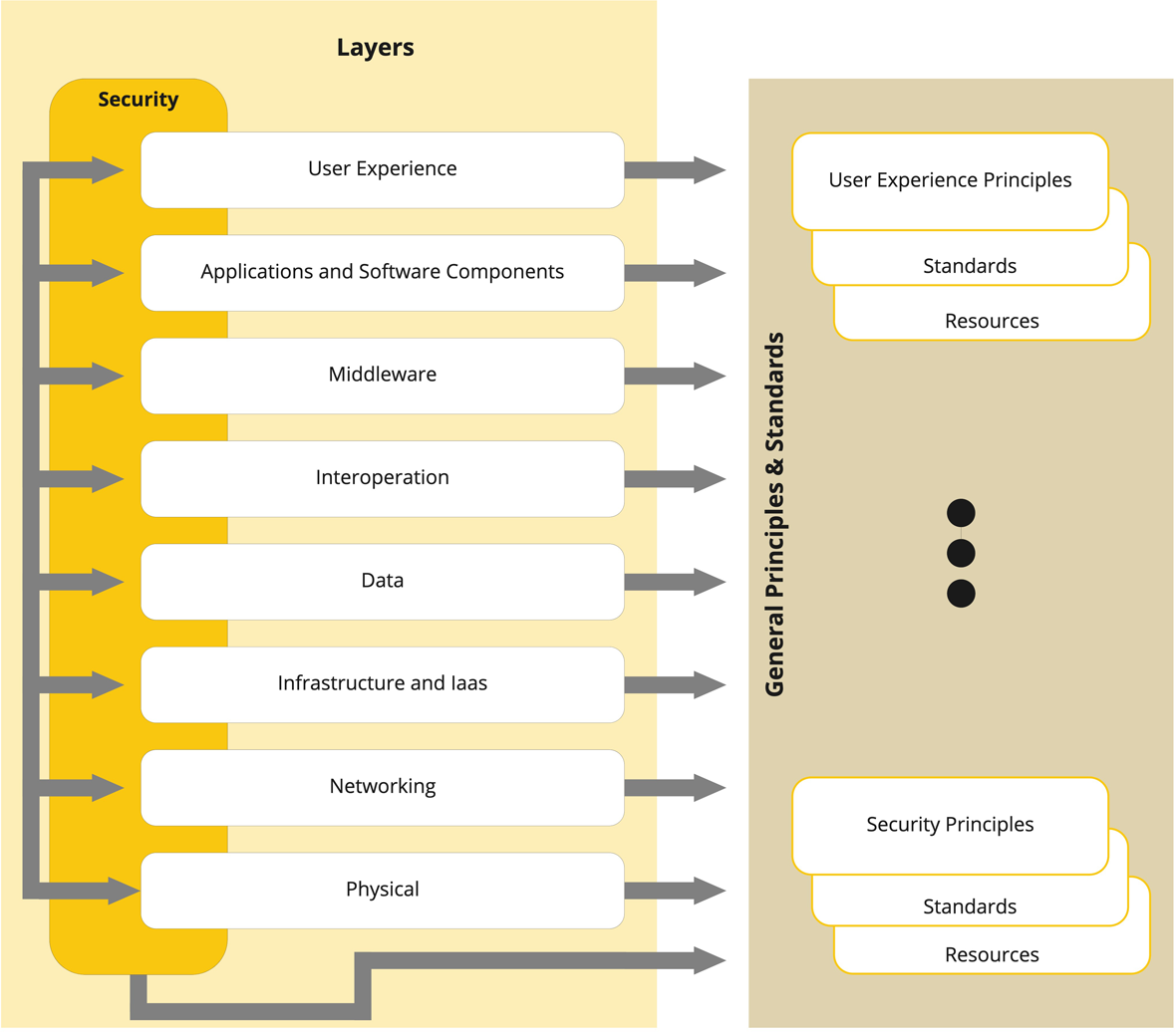
Architecture Layers
- Explore the Layers
- Security
- User Experience
- Applications
- Middleware
- Interoperation
- Data
- Infrastructure
- Network
- Physical
Security
User Experience
User Experience is a core consideration when designing, selecting, and delivering tools and services to the Harvard community.
In order to improve user productivity, reduce frustration, and increase effectiveness for all users, user experience methods and techniques are applied across the full systems development lifecycle, with a focus on: accessibility, ussbility, and mobility.
Applications
Applications reflect the most direct alignment of Information Technology solutions to business requirements. As such they must deliver the appropriate 'fit, form, and function' to the business owners. In addition, supportability and total cost of ownership are considerations that the IT community requires.
Evolution and reinvestment in applications are driven in part by changing business requirements, but also in part by transitions in technologies such as web-based applications, and cloud computing. EA provides 'road maps' to help chart the implementation of new and evolving applications to meet business needs.
Middleware
Middleware has historically reflected Information Technology solutions that could be shared by multiple users, such as shared Oracle databases.
Contemporary trends in computing have enlarged this concept to include difficult-to-implement but common capabilities such as authentication, authorization, access control, API management, security management, monitoring, logging, and other capabilities. Thus the role of Middleware is to provide complex services to application teams in an approachable and robust way.
Interoperation
Combining data from disparate sources into meaningful and valuable information is increasingly important to effective support of business needs. Enterprise Architecture works to support these integration requirements by aligning people, processes and tools across the University.
Data
Data and information are key University assets that must be managed to maximize value and minimize risk.
Enterprise Architecture works to support this goal through the development of data models and documentation, data access policies, and data governance processes.
Infrastructure
Infrastructure encompasses hardware and virtualized platforms that operate applications, services, and their components.
The hardware elements of Harvard’s IT capability must be aligned with the organization's business goals. Enterprise Architecture works to define, design and align the sum of Harvard’s physical and virtual infrastructure to ensure efficient and effective support of business applications.
Network
The Architectural Layers
We approach the work of defining an architecture for the University by considering each layer of our physical architecture "stack", as well as cross-cutting security requirements, and articulating a set of Principles, Standards and Resources for each layer.